Lorem ipsum generator · MAC address lookup or manufacturer lookup · Markdown to HTML converter · MD5, SHA1, SHA224, SHA256, SHA384, SHA512 and RIPEMD160 hash generator · Mugshot maker · Nominal interest rate and effective interest rate converter · One-time pad encoder/decoder and key generator ·
SHA512 Generator · Crontab Generator · Lorem Ipsum Text Generator · Generate the SHA512 hash of any string. The SHA512 hash can not be decrypted if the text you entered is complicated enough.
SHA512 Generator · Crontab Generator · Lorem Ipsum Text Generator · Generate Lorem Ipsum Text ·
Donec auctor, nulla nec malesuada maximus, purus neque accumsan metus, eget luctus sapien mauris id lorem. Nunc fermentum neque consectetur porttitor sollicitudin. Donec consequat sapien eros, et molestie leo gravida at. Morbi ut dictum lacus, ut imperdiet massa. In ultrices ipsum maximus, imperdiet risus non, molestie libero.
Easily generate dummy text with the Lorem Ipsum generator.
Lorem ipsum, or lipsum as it is sometimes known, is dummy text used in laying out print, graphic or web designs. The passage is attributed to an unknown typesetter in the 15th century who is thought to have scrambled parts of Cicero's De Finibus Bonorum et Malorum for use in a type specimen book.
crypto_sha512_hmac() is a convenience function that performs crypto_sha512_hmac_init(), crypto_sha512_hmac_update(), and crypto_sha512_hmac_final(). These functions return nothing. ... uint8_t hash [64]; /* Output hash (64 bytes) */ uint8_t message[12] = "Lorem ipsum"; /* Message to hash */ crypto_sha512(hash, message, 12);
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem.
Lorem ipsum is a pseudo-Latin text used in web design, typography, layout, and printing in place of English to emphasise design elements over content. It's also called placeholder (or filler) text. It's a convenient tool for mock-ups. It helps to outline the visual elements of a document or ...

Base64 Encoder & Decoder URL Encoder & Decoder MD5 Hash Generator SHA1 Hash Generator SHA3 Hash Generator SHA256 Hash Generator SHA512 Hash Generator Multiple Hash Generator · SMS Counter Check String Length Password Generator · QR Code Generator Lorem Ipsum Generator HTML Entities MIME Types Table Reference What Is My IP Address

Easily generate Lorem Ipsum placeholder text in any number of characters, words sentences or paragraphs. Learn about the origins of the passage and its history, from the Roman era to today.
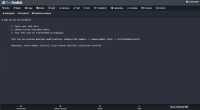
Lorem Ipsum Strings Numbers Passwords Emails IPs UUIDs MACs Dates Names · Generate · 3 paragraphs · 4 paragraphs · 5 paragraphs · 6 paragraphs · 7 paragraphs · Length · Short · Medium · Long · Format · Text · HTML Generate · Line Length · Lines Letters Numbers Specials Spaces Generate strings ·

Lorem Ipsum Generator. Generate lorem ipsum in paragraphs, words or sentences. Optional html markup - paragraph, italic and bold tags.
Need random text for your project? Our Lorem Ipsum Generator lets you easily generate filler text. Choose the number of paragraphs, words, or characters you need.
This free lorem ipsum generator lets you choose how many sentences, paragraphs or list items you want. You can also select to include HTML markup and specify how big the text should be.
Lorem Ipsum Generator · List of MIME types · HTML Entities · Url Parser / Query String Splitter · I18N Standards / Code Snippets · Computes a digest from a string using SHA-512. Learn more about SHA-512 in the SHA-512 explained section of this page. I use Bouncy Castle for the implementation.
Easily generate dummy text with the Lorem Ipsum generator.
To Generate Lorem Ipsum, simply select your desired settings below and hit generate.
Lorem Ipsum Generator · Invisible Character & Blank Text · Simplified Traditional Chinese Converter · Text Case Converter · Morse Code Translator · Text Compare · Text Word Counter · Find and Replace Text · Text to ASCII Art Converter · Duplicate Remover ·
BLAKE2b CRC32 Keccak256 MD5 RIPEMD-160 SHA-1 SHA224 SHA256 SHA3-256 SHA3-384 SHA3-512 SHA384 SHA512 Whirlpool